Beware of these 7 new hacker tricks — and how to protect yourself
Following the huge wave of ransomware last year, there’s now increasing reports of completely new tricks used by hackers and cybercriminals to gain access to computer systems, devices, and networks.
Many of these tricks exploit existing vulnerabilities in applications and operating systems, but these perpetrators are also developing completely new approaches that combine technical procedures with social engineering to achieve their goals.
To recap if you’re unaware: social engineering is when a malicious person exploits you through helpfulness, trust, fear, or respect in an attempt to manipulate you into doing something.
Further reading: Key signs of social engineering to look for
Examples of social engineering include: a work email purporting to come from your boss with a payment order for a large sum to a foreign account; a WhatsApp message from someone pretending to be your relative in need of money; or a phishing email that claims to be your bank asking you to click a link with scary consequences if you don’t.
Here are some of the latest scams and techniques used by criminals that you need to know about—and how you can protect yourself.
1. The zero font trickIt’s possible to set the font size of email text to zero using HTML code. In this way, the text is present but not visible to the eye.
A few years ago, criminals used this trick to insert invisible text into messages in order to fool the spam and virus detection mechanisms of email providers and mail programs.
They used this technique to insert harmless words and phrases into the email body to make the message appear safe, thus outwitting the email providers’ malware filters.
For emails in HTML format, it’s possible to set the font size to zero. The corresponding attribute is “font-size:0”.

For emails in HTML format, it’s possible to set the font size to zero. The corresponding attribute is “font-size:0”.
IDG

For emails in HTML format, it’s possible to set the font size to zero. The corresponding attribute is “font-size:0”.
IDG
IDG
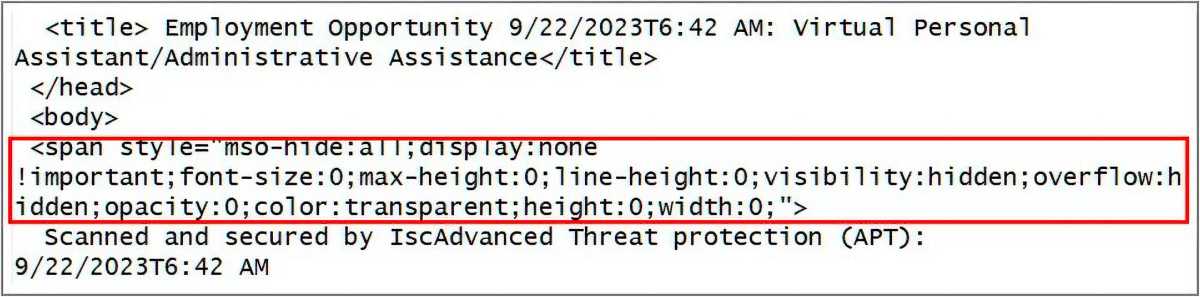
Last autumn, security researcher Jan Kopriva became aware of a new version of the zero font trick. Hackers used it to attack Microsoft Outlook users, exploiting a feature of the program’s email display.
The issue is that Outlook happens to display zero font text in its list view, but not in the email preview. The malicious senders therefore placed the zero-point text in the message: “Isc Advanced Threat protection: This message has been scanned for threats.”
“Isc” stands for the Internet Storm Center, an organization of the SANS Institute that monitors malicious activity on the internet. The reference to the alleged malware scan made the email seem trustworthy to recipients, so they were more inclined to open it and trust what it says.
However, the message actually contained a link to a fake website that requested the visitor’s access data:
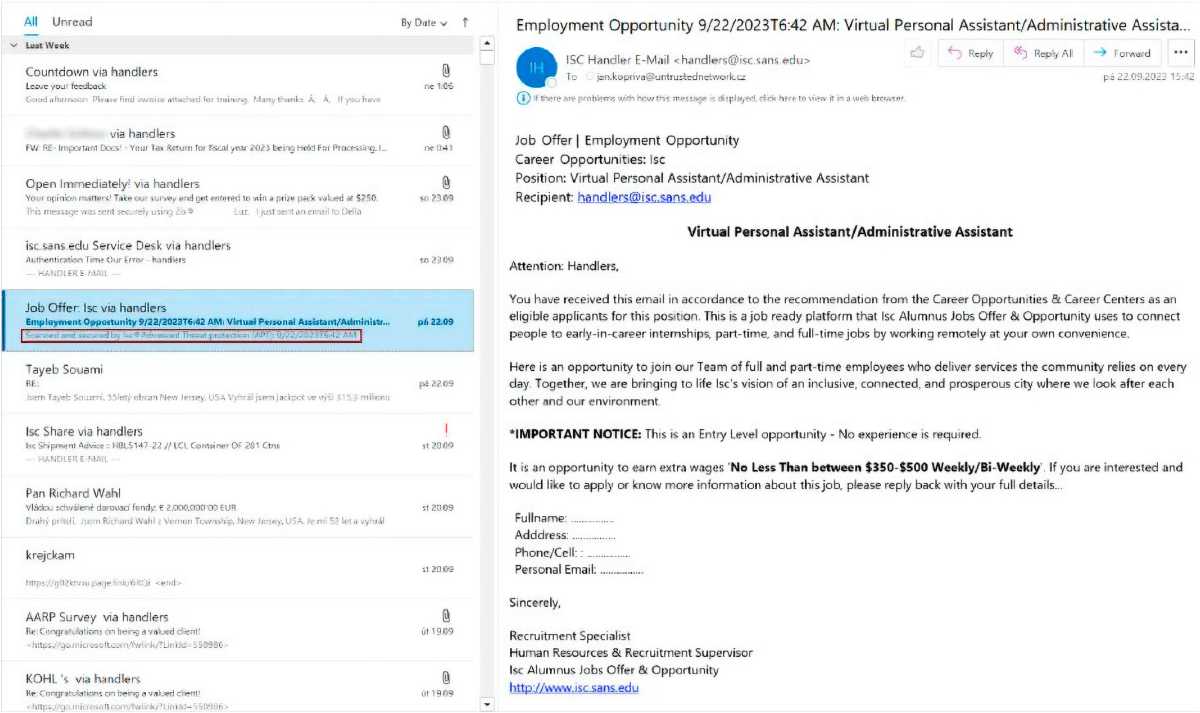
Outlook displays zero font text in the list view. The email has supposedly already been scanned for malware threats and is harmless. It therefore appears trustworthy to the recipient.

Outlook displays zero font text in the list view. The email has supposedly already been scanned for malware threats and is harmless. It therefore appears trustworthy to the recipient.
IDG

Outlook displays zero font text in the list view. The email has supposedly already been scanned for malware threats and is harmless. It therefore appears trustworthy to the recipient.
IDG
IDG
How to protect yourself:
- Learn how to spot scam emails and messages.
- Even with emails that claim to be from reputable senders, remember that they could be fake.
- Hover over every link to confirm the destination address before clicking—and even then, don’t click unless absolutely necessary. It’s better to navigate to the site manually if you can.
- If you have any doubts that an email actually came from a particular sender, give them a quick call to confirm.
Two-factor authentication (2FA) or multi-factor authentication (MFA) protects users against attacks on their login credentials. With 2FA enabled, it’s much harder to hack an account.
So, hackers are increasingly trying to access the cookie files that are created during the login process that certify correct authentication.
With these session cookies, it’s possible for a user to log in just once and continue accessing various services. As soon as the user logs out, the session cookie is deactivated.
Further reading: How to use 2FA the right way
Various malware programs are now exploiting a vulnerability in the Google login process to reactivate expired session cookies. In this way, they can freely access all Google services belonging to a user.
This works even if they’ve changed their password in the meantime. However, this requires the malware to have access to the user’s computer.
How to protect yourself:
- Understand how malware infections happen. Don’t open attachments in suspicious emails. Don’t click on links in emails. Don’t download apps from illegal or suspicious sites.
- Shut down your computer when you don’t need it.
- Apply security patches for Windows and other programs immediately and always keep your software up to date.
Traditionally, the boss scam is where your “boss” instructs you to transfer a large sum of money to an unusual account, but the “boss” is actually a hacker who’s sending your fraudulent emails or texts.
A new variant has now come to light in Hong Kong, where hackers invited their victim to a video conference by email. However, no real people were waiting for him there—only deepfakes of colleagues from his company. (A deepfake is an AI-generated impersonation of a real person.)
These deepfakes instructed the victim to carry out 15 transfers totaling 200 million Hong Kong dollars. (About $26 million USD.) The victim only realized that he had been scammed when he later spoke to his boss.
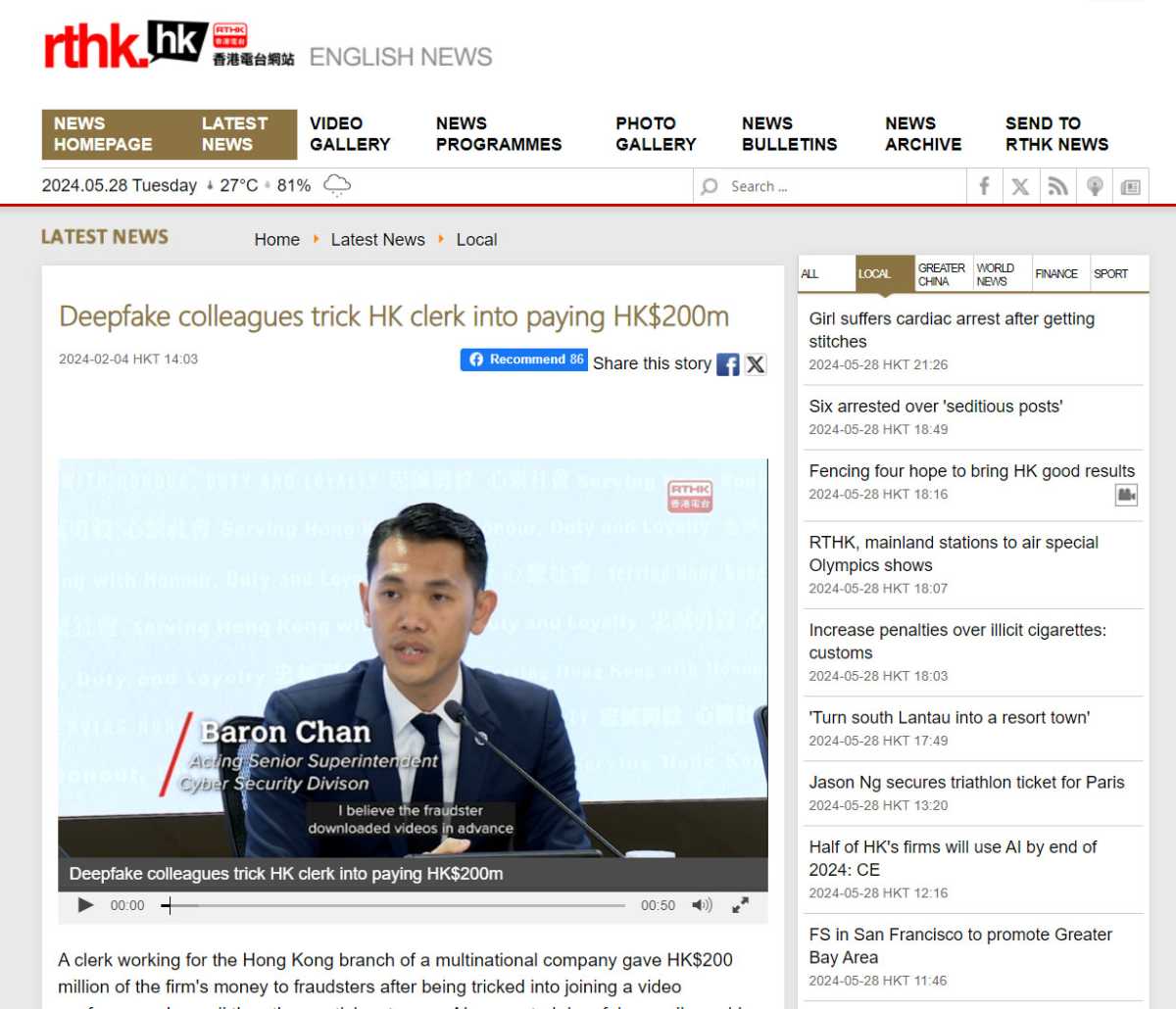
Baron Chan, head of the cybersecurity department of the Hong Kong police, suspects that the criminals had previously downloaded videos of the company’s employees for the deepfake of a video conference.

Baron Chan, head of the cybersecurity department of the Hong Kong police, suspects that the criminals had previously downloaded videos of the company’s employees for the deepfake of a video conference.
IDG

Baron Chan, head of the cybersecurity department of the Hong Kong police, suspects that the criminals had previously downloaded videos of the company’s employees for the deepfake of a video conference.
IDG
IDG
The cybersecurity department of the Hong Kong police suspects that the criminals had copied videos of their real colleagues from the company’s servers and combined that with AI-supported voice synthesis to create the deepfakes used in the video conference.
How to protect yourself:
- Hong Kong police advise people to ask questions during video conferences to verify the identities of other participants.
Word has gotten around that AI-supported language models like ChatGPT are hallucinating (i.e., making up information). For example, AI chatbots have invented court judgments for trials that have never taken place. But they can also hallucinate non-existent software packages.
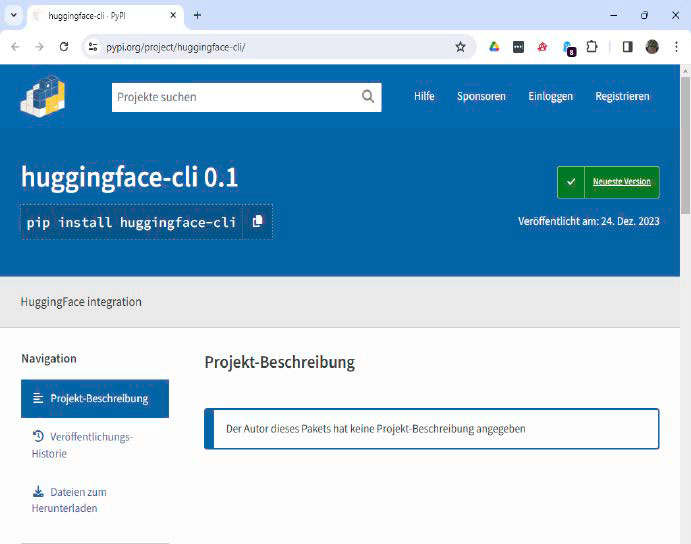
A security researcher placed the package huggingface-cli in the Python Package Index (PyPI). In fact, an AI had only invented the package. Nevertheless, it was used by several Python projects within a few weeks.

A security researcher placed the package huggingface-cli in the Python Package Index (PyPI). In fact, an AI had only invented the package. Nevertheless, it was used by several Python projects within a few weeks.
IDG

A security researcher placed the package huggingface-cli in the Python Package Index (PyPI). In fact, an AI had only invented the package. Nevertheless, it was used by several Python projects within a few weeks.
IDG
IDG
Israeli security researcher Bar Lanyado asked himself what would happen if real code were to be published under a name invented by AI.
He asked ChatGPT-3.5-Turbo, ChatGPT-4, Gemini Pro, and Cohere Command for help with a programming problem and identified a piece of code with the name huggingface-cli that had been repeatedly recommended over several months but didn’t actually exist.
He then created an empty Python package with this name and put it online. Within a few weeks, it had been downloaded 15,000 times. Also, a GitHub search revealed that huggingface-cli had appeared in the repositories of several large companies.
The Python package from Bar Lanyado might be a harmless file with no content or consequences, but you can imagine how hackers could distribute malicious code in the same way.
How to protect yourself:
- Programmers should never blindly trust the suggestions of AI models and should double-check recommended downloads themselves.
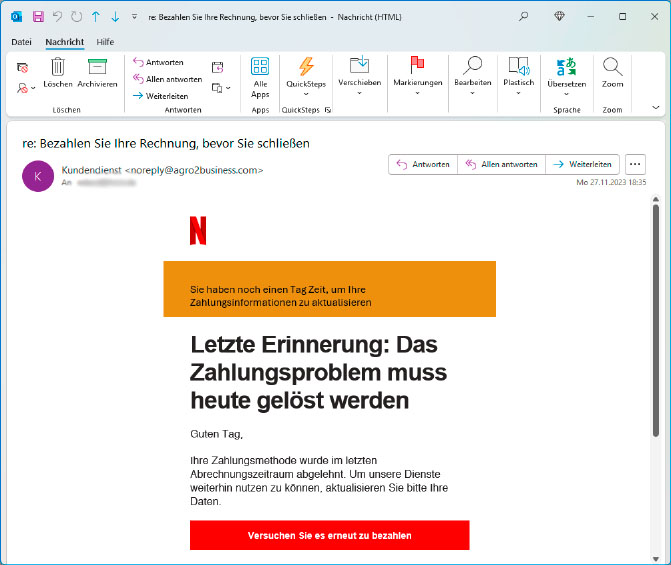
Typical of modern phishing emails are the time pressure they create and phrases such as “Start confirmation” or “Try to pay again.”

Typical of modern phishing emails are the time pressure they create and phrases such as “Start confirmation” or “Try to pay again.”
IDG

Typical of modern phishing emails are the time pressure they create and phrases such as “Start confirmation” or “Try to pay again.”
IDG
IDG
Fraudsters use phishing emails to try to persuade you to visit fake websites or websites infected with malware.
They usually ask you to enter your address and/or login details. You will then receive a phone call in which the criminals ask for a PIN or some other security factor. Or they simply sell your access data, such as your login credentials to your Netflix account.
Many of these phishing emails follow the same pattern: under a short introductory text is a button that takes you to the fake website. In many cases, the email uses a scare tactic or time pressure so that you don’t think about the authenticity and plausibility of the message.
Common button captions include:
- “Update account now”
- “Update address”
- “Confirm now”
- “Win now”
- “Go to account recovery page”
- “Stay protected” (for emails purporting to be from security vendors)
- “Show order details”
- “Activate now”
- “Try to pay again”
- “Pay fee now”
You should never click on any of these buttons. Always remember that reputable companies—including banks and online retailers—will never ask you to enter your login details by email.
6. Proxy server as an appCybercriminals often face a common problem: the IP addresses of their control servers and botnets end up on blacklists, and they’re subsequently blocked by providers, companies, and organizations.
To avoid this, they redirect their data packets via proxy servers, effectively giving new IP addresses to those data packets. But then these public proxy servers also end up on blacklists. It’s a vicious cycle.
But they have a new trick now: using malware to turn the smartphones and desktop PCs of unsuspecting users into proxy servers.
In May 2023, security researchers noticed an app in the Google Play Store that secretly turned smartphones into proxies. They later searched and found a total of 28 apps with PROXYLIB, which is responsible for these hidden proxy servers. All of them were VPN apps that supposedly provided encrypted connections on the internet.
Google has now integrated a detection routine for proxy malware in the Play Protect protection mechanism, which automatically deletes the apps in question. However, don’t be surprised if alternative app stores continue to make these malware-infected apps available.
How to protect yourself:
- There’s a list of malicious apps at the bottom of this webpage. If you have one or more of them installed, delete them as soon as possible.
- Only install apps via the Google Play Store.
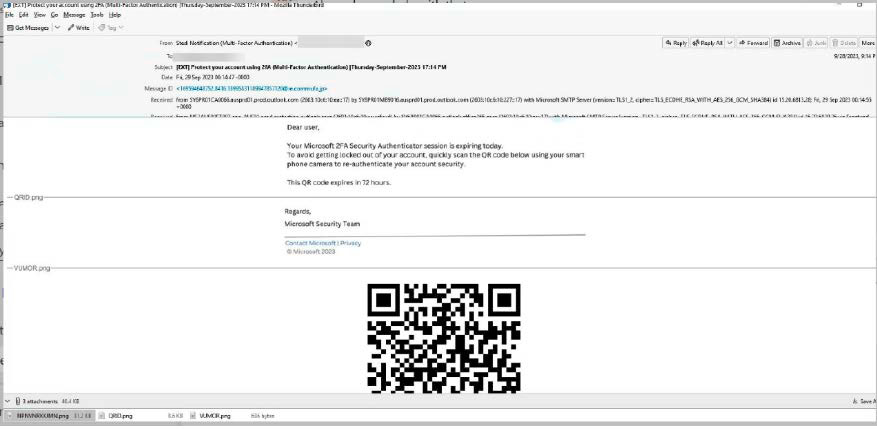
QR codes don’t reveal the destination of a link at first glance. In this quishing email purporting to be from Microsoft, the link in the image leads to a fake Microsoft login page.

QR codes don’t reveal the destination of a link at first glance. In this quishing email purporting to be from Microsoft, the link in the image leads to a fake Microsoft login page.
IDG

QR codes don’t reveal the destination of a link at first glance. In this quishing email purporting to be from Microsoft, the link in the image leads to a fake Microsoft login page.
IDG
IDG
Phishing is a type of scam where an email or message is sent to a prospective victim in hopes that they’ll click a malicious link within. It’s been around for several years now, and email providers have gotten better at recognizing and filtering out phishing attempts.
Because of that, hackers are exploring other methods of luring victims to their sites—like quishing, the transmission of links via QR code. (Quishing is also known as QR phishing.)
You’ve probably scanned QR codes with your smartphone to read restaurant menus, enter contests, and more. Hackers exploit this behavior by integrating QR codes into their emails, which then lead you to fake login pages or otherwise malicious pages.
Last autumn, the security company Harmony reported a 587 percent increase in quishing attacks.
Security provider Check Point also describes a quishing attack in which users were directed to a fake Microsoft login page. In this way, the attackers were able to bypass the usual security measures used to filter out phishing messages.
How to protect yourself:
- Always pay attention to who sent you an email with a QR code and take a close look at the address displayed by the QR code reader. When in doubt, avoid scanning unsolicited QR codes.
This article was translated from German to English and originally appeared on pcwelt.de.
Security Software and Services